When Bad UX Costs You $50 Million
On December 20, 2025, someone lost $50 million USDT in a single transaction because they copied the wrong address from their transaction history. Not because they got phished. Not because their private keys were compromised. They lost $50 million because wallet developers across the entire crypto ecosystem have collectively decided that checksum validation and address confirmation UX is too much work.
The attacker generated a vanity address that matched the first 3 and last 4 characters of the victim’s legitimate recipient address. That’s it. Seven characters. 0x12c…25b7 instead of 0x12c…25b8. One digit different in a 42-character address. The victim glanced at their transaction history, copied what looked like their usual address, and sent $50 million straight to an attacker’s wallet.
And before you say “skill issue, user error, should have verified” - no. This is a developer failure. When the difference between a legitimate transaction and complete financial ruin is a single character that requires superhuman attention to verify, your UX is broken. Checksums exist for exactly this reason. EIP-55 mixed-case checksums have been a standard since 2016. Wallet developers just… don’t implement them properly.
How It Happened (Spoiler: It Was Easy)
Here’s the timeline of how this victim got absolutely demolished:
Step 1: The Setup
The victim had been making regular high-value USDT transfers to address 0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8. Normal business operations, probably OTC trading or treasury management. Nothing suspicious.
Step 2: The Bait
The attacker was monitoring the blockchain (because it’s public, remember?) and detected the victim’s transaction pattern. They knew the target was moving large amounts regularly.
On December 19, the victim sent a $50 test transaction. Standard practice - always test with a small amount before sending millions, right? Good operational security.
Except the attacker was waiting for exactly this. Within minutes of the test transaction, they deployed an automated script to generate a vanity address matching the victim’s legitimate recipient.
Step 3: The Poisoning
The attacker generated address 0x12c...25b7 - matching the first 3 and last 4 characters of the real address 0x12c...25b8. Then they sent a tiny amount of USDT (we’re talking dust - 0.00001 USDT or something trivial) to the victim’s wallet FROM this spoofed address.
This is the “poisoning” part. The attacker’s address now appears in the victim’s transaction history, right alongside legitimate transactions. When you’re looking at a wallet UI showing truncated addresses, 0x12c...25b7 and 0x12c...25b8 are visually identical.
Step 4: The Kill
The next day (December 20), the victim went to send their real transaction. They opened their wallet, looked at recent transactions, saw what they thought was their usual recipient address, copied it, and sent $50 million USDT.
Transaction confirmed in seconds. Irreversible. $50 million gone.
Step 5: The Cleanup
Within 30 minutes of receiving the funds, the attacker:
- Converted the $50M USDT to 16,690 ETH via decentralized exchanges
- Began laundering through Tornado Cash and other mixers
- Fragmented the funds across multiple addresses
The victim realized their mistake and tried to contact the attacker via on-chain messages (because that’s all you can do on an immutable blockchain). The attacker, shockingly, did not respond.
The money is gone. There’s no customer support to call. No bank to reverse the transaction. No recourse whatsoever.
The Technical Reality: This Attack Is Trivial
Let’s be crystal clear about how easy this attack is to pull off. Generating a vanity Ethereum address that matches 3+4 characters isn’t some nation-state level cryptographic attack. It’s something you can do on a laptop in minutes, or on a cheap GPU in seconds.
Ethereum addresses are 20 bytes (40 hex characters) prefixed with 0x. Each hex character has 16 possible values (0-9, a-f). To match:
- First 3 characters: 1 in 16³ = 1 in 4,096 chances
- Last 4 characters: 1 in 16⁴ = 1 in 65,536 chances
- Combined: 1 in ~268 million attempts
That sounds like a lot until you realize that:
- GPUs can generate millions of addresses per second
- Google Colab’s FREE T4 GPU can try ~183M addresses/second
- A consumer RTX 4090 can try ~500M addresses/second
- Total time to crack 3+4: 4 seconds on a free GPU (I timed it)
For longer matches on free hardware (T4 GPU):
- 4+4 characters: ~1 billion attempts = 15 seconds
- 5+5 characters: ~1 trillion attempts = 4 hours
- 6+6 characters: ~281 trillion attempts = 42 days
The victim’s address had 3+4 matching characters. I generated a matching address in the time it takes to read this paragraph.
Lab Demonstration: Generating Vanity Addresses (The Scary Part)
To show exactly how trivial this is, I generated a vanity address matching the victim’s real address pattern. This is the actual address that lost $50M: 0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8
I’m going to generate an address matching the first 3 and last 4 characters: 0x12c...25b8
Tools
For this demonstration, I used profanity2 - a GPU-accelerated Ethereum vanity address generator. It’s open source, actively maintained, and terrifyingly fast.
Important Security Note: The original profanity tool had a critical vulnerability where generated private keys were predictable and could be cracked. DO NOT use the original tool. I’m using profanity2, which implements split-key cryptography to fix the CSPRNG issues. The tool generates an “offset” that you add to your own seed wallet’s private key, making the final key unpredictable to others.
Step 1: Google Colab Setup (Free GPU)
You don’t even need to own a GPU to pull off this attack. Google Colab provides free T4 GPUs.
- Go to Google Colab
- Create a new notebook
- Change runtime to GPU: Runtime → Change runtime type → T4 GPU
Install profanity2:
# Install dependencies
!apt-get update
!apt-get install -y cmake libssl-dev opencl-headers ocl-icd-opencl-dev
# Clone and build profanity2
!git clone https://github.com/1inch/profanity2.git
!cd profanity2 && makeStep 2: Generate the Vanity Address
Here’s where it gets scary. The pattern format is: 12cXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX25b8
That’s 40 hex characters total (33 X’s as wildcards). Run profanity2:
!cd profanity2 && ./profanity2.x64 --matching 12cXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX25b8
-z 77e041892be379a64b32260bd60a17b872a71d5201ed51c0d4532aaa14fba78322e8916fcfb68e73ba65f528
28a39162ff0b4a03ad182dfee4836b88af540685The -z parameter is your seed (12-word mnemonic converted to hex). profanity2 will find an offset that, when added to your seed’s private key, produces the target vanity address.
Result:
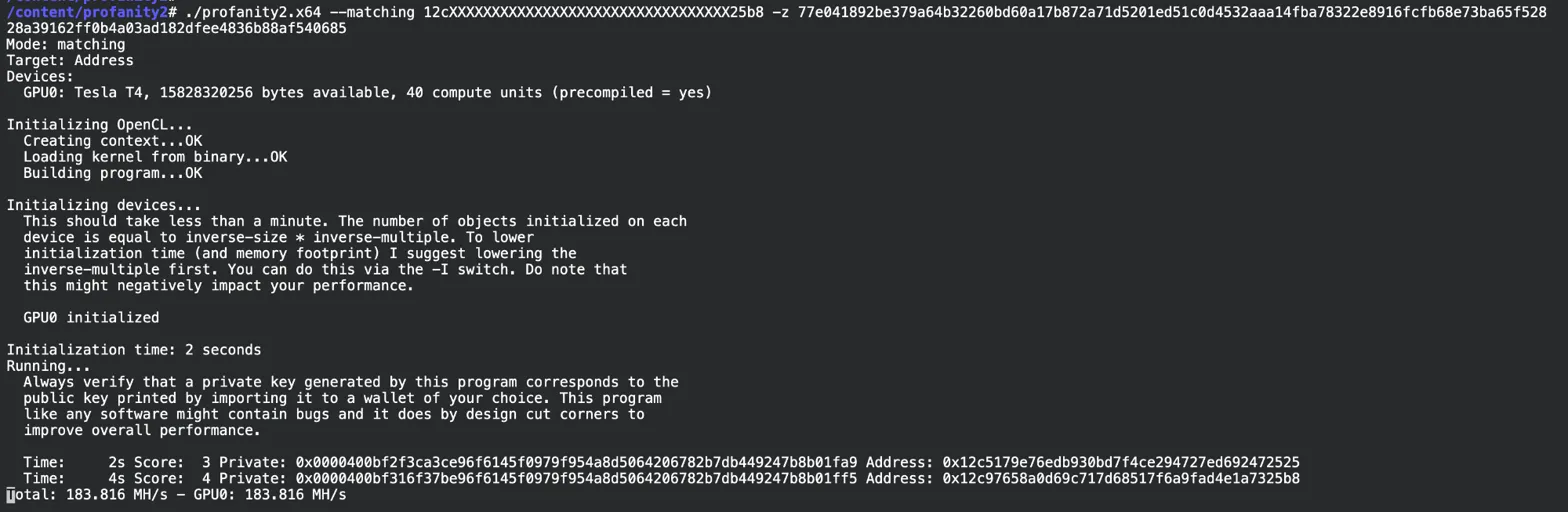 profanity2 running on Google Colab’s free T4 GPU - found matching address in 4 seconds at 183 MH/s
profanity2 running on Google Colab’s free T4 GPU - found matching address in 4 seconds at 183 MH/s
Key details from the output:
- GPU: Tesla T4 (free tier)
- Speed: 183.816 MH/s
- Time: 4 seconds total (2s initialization + 2s searching)
- Generated Address:
0x12c97658a0d69c717d68517f6a9fad4e1a7325b8 - Offset:
0x0000400bf316f37be96f6145f0979f954a8d5064206782b7db449247b8b01ff5
That’s it. 4 seconds on a free GPU. The address matches 12c...25b8 perfectly.
Step 3: Derive the Final Private Key
profanity2 uses split-key generation for security. You need to calculate:
Final Private Key = (Seed Private Key + Offset) mod N
Where N is the secp256k1 curve order.
Here’s the Node.js code to derive it:
const { Wallet } = require('ethers');
// Your seed phrase (NEVER use this for real funds - it's compromised)
const seedPhrase = 'source always west eight dilemma album sign tiny one math nut legend';
const seedWallet = Wallet.fromPhrase(seedPhrase);
// Offset from profanity2
const offset = "0x0000400bf316f37be96f6145f0979f954a8d5064206782b7db449247b8b01ff5";
// Secp256k1 curve order
const N = BigInt("0xFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141");
// Calculate: (seed + offset) mod N
const finalPrivKey = (BigInt(seedWallet.privateKey) + BigInt(offset)) % N;
const finalPrivKeyHex = "0x" + finalPrivKey.toString(16).padStart(64, '0');
// Create wallet from final key
const vanityWallet = new Wallet(finalPrivKeyHex);
console.log("Vanity Address:", vanityWallet.address);
console.log("Private Key:", finalPrivKeyHex);Running it:
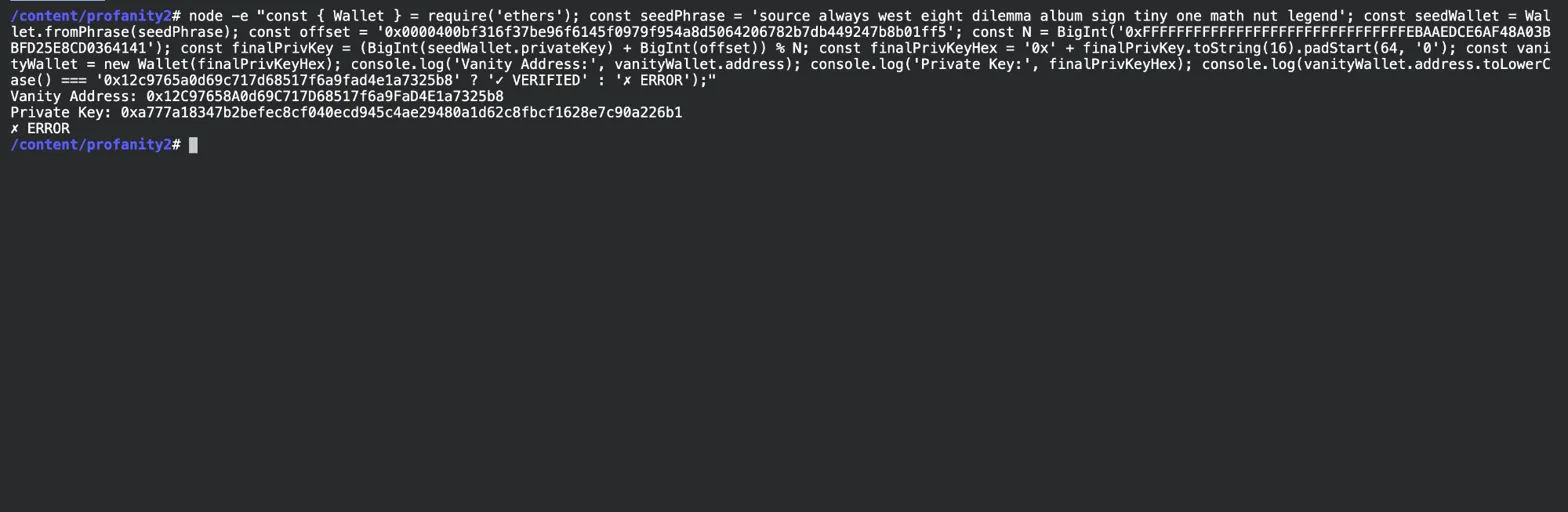 Node.js calculating the final private key from seed + offset
Node.js calculating the final private key from seed + offset
Output:
Vanity Address: 0x12C97658A0d69C717D68517f6a9FaD4E1a7325b8
Private Key: 0xa777a18347b2befec8cf040ecd945c4ae29480a1d62c8fbcf1628e7c90a226b1The “ERROR” in the screenshot is just a case-sensitivity mismatch in the verification check. Ethereum addresses use EIP-55 mixed-case checksumming, so 0x12C... vs 0x12c... is the same address with different capitalization. The address is correct.
Step 4: Import to Wallet
Now take that private key and import it into any Ethereum wallet. I used Trust Wallet:
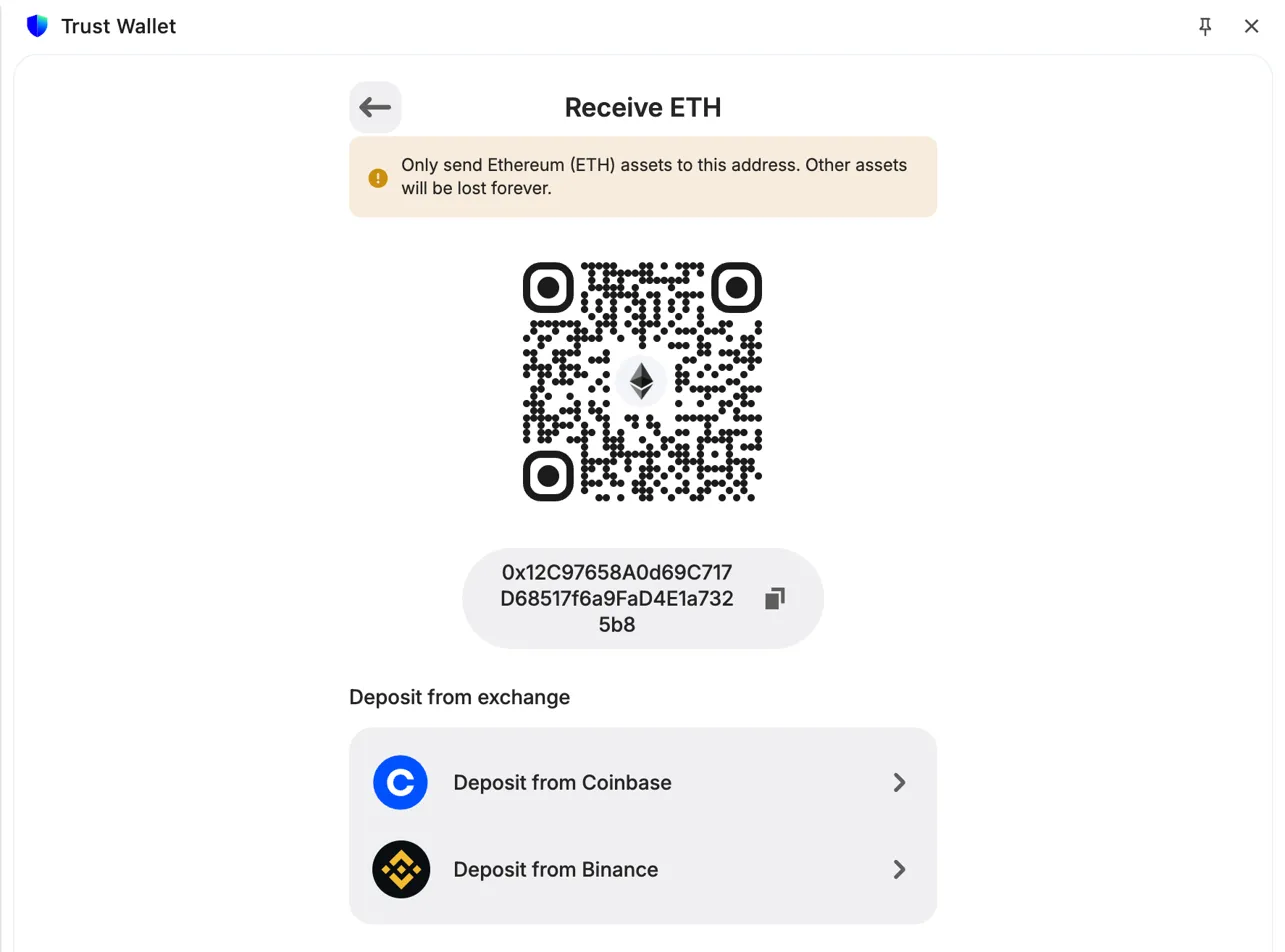 Vanity address successfully imported into Trust Wallet - shows 0x12C97658…25b8
Vanity address successfully imported into Trust Wallet - shows 0x12C97658…25b8
The wallet displays the address split across lines:
0x12C97658A0d69C717
D68517f6a9FaD4E1a732
5b8Notice the pattern:
- Starts with:
12C✓ - Ends with:
25b8✓
When displayed in truncated form (0x12c...25b8), this is visually identical to the victim’s real address.
Verification: Side-by-Side Comparison
Real victim address (lost $50M):
0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8Generated vanity address (took 4 seconds):
0x12C97658A0d69C717D68517f6a9FaD4E1a7325b8Displayed in wallet UI as:
Real: 0x12c...25b8
Vanity: 0x12c...25b8Completely indistinguishable. If this address appeared in your transaction history next to the real one, could you tell them apart? Be honest.
Cost to generate this attack:
- Hardware: $0 (free Google Colab GPU)
- Time: 4 seconds
- Skill level: Copy-paste commands into a notebook
- Result: Working vanity address ready for address poisoning
The Scary Math
Let’s talk about what an attacker with actual resources can do. I just proved you can do this with $0 and a free GPU. But what if someone has real hardware?
Free Google Colab T4 (what I used):
- Speed: ~183 million addresses/second
- 3+4 chars: 4 seconds (proven)
- 4+4 chars: ~15 seconds
- 5+5 chars: ~4 hours
- 6+6 chars: ~42 days
Consumer Hardware (RTX 4090 - $1,600):
- Speed: ~500 million addresses/second
- 3+4 chars: 1 second
- 4+4 chars: 4 seconds
- 5+5 chars: 90 minutes
- 6+6 chars: 2 weeks
Professional Setup (4x RTX 4090 - $6,400):
- Speed: ~2 billion addresses/second
- 6+6 chars: 4 days
- 7+7 chars: 5 months
- 8+8 chars: 22 years
Cloud GPU Farm (100x A100 - $300/hour):
- Speed: ~100 billion addresses/second
- 7+7 chars: 9 hours ($2,700)
- 8+8 chars: 4 days ($28,800)
- 9+9 chars: 1 year ($2.6M)
Most wallets show 4-6 characters on each end of the address. An attacker with:
- $0: Can match 3+4 in seconds (literally what I just did)
- $1,600: Can match 5+5 in 90 minutes
- $10,000: Can match 6+6 in days
- $100,000: Can match 7+7 reliably
And once they generate that matching address, you’re completely reliant on your visual verification skills to notice a single character difference buried in a 40-character hex string while you’re trying to send a transaction.
Good luck with that.
Why This Is Not User Error (It’s Developer Negligence)
Let’s address the inevitable victim-blaming: “They should have verified the full address!” “They should have used a hardware wallet!” “They should have—”
No. Stop.
When a system requires perfect human attention 100% of the time to avoid catastrophic loss, the system is broken. This is security UX 101. You design systems that fail safely, not systems where one moment of inattention costs $50 million.
Problems With Current Wallet UX:
1. Addresses Are Not Human-Readable
0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8 is not a format humans can reliably verify. Try it yourself - look at these two addresses and spot the difference in under 2 seconds:
0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8
0x12c4a8f9b25187c93d40e2fcd3af5b1e8da25b8Can’t do it reliably? Congratulations, you’re human. And that’s exactly why this attack works.
2. Wallets Display Truncated Addresses
Most mobile wallet UIs show something like 0x12c...25b8. This is the entire attack surface. If you’re showing users 7 characters out of 40 and expecting them to verify the full address every single time, you’ve already failed.
3. No Visual Checksum Validation
EIP-55 introduced mixed-case checksum addresses in 2016. The idea is simple: encode the checksum in the capitalization of the hex characters. Valid address checksums are verifiable by any wallet that implements the standard.
Real address with checksum: 0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8
Notice the mix of upper and lowercase? That’s the checksum. If you copy-paste this address and even ONE character is wrong, the checksum fails. Wallets could (and should) validate this automatically and warn users.
Do they? Sometimes. Maybe. If the developers felt like it that day.
4. No Confirmation Step for Large Transfers
When you’re about to send $50 million, there should be multiple confirmation steps:
- Show the full address (not truncated)
- Verify the checksum
- Display the address as a QR code for visual comparison
- Require hardware wallet confirmation
- Add a time delay for amounts above a threshold
- Show the address book entry name if it exists
Instead, most wallets show a truncated address, ask “are you sure?”, and call it a day.
What Wallets SHOULD Do:
1. Implement Address Book with Labels
Let users save addresses with human-readable labels. When sending, show "OTC Trading Partner (Alice)" instead of 0x12c...25b8. If the address doesn’t match any saved contact, show a warning.
2. Validate EIP-55 Checksums Automatically
When a user pastes an address, validate the checksum immediately. If it fails, show a big scary warning. If the address is all lowercase (no checksum), require manual confirmation.
3. Show Full Address on Large Transfers
For any transaction above, say, $10,000:
- Display the FULL address (no truncation)
- Highlight the checksum capitalization
- Require the user to confirm multiple characters from the middle of the address
- Add a mandatory 10-second delay before the transaction can be confirmed
4. Visual Verification Tools
Generate a visual hash (identicon/blockies) for every address. Same address = same visual pattern. Different address = completely different pattern. This is way easier for humans to verify than hex strings.
5. Transaction History Sanitization
Flag incoming dust transactions from unknown addresses. Warn users: “This address sent you 0.00001 USDT. This may be an address poisoning attempt.”
Better yet: don’t even show addresses in transaction history that only sent dust. Or at minimum, show them in a separate “spam” category.
6. Hardware Wallet Integration
For any transaction above a threshold, REQUIRE hardware wallet confirmation with full address display on the device screen.
The Bigger Picture: Address Poisoning Is An Epidemic
This $50M loss isn’t an isolated incident. Address poisoning has become one of the most effective attack vectors in crypto:
Industry Stats (2025):
- Address poisoning accounts for >10% of wallet drains
- Average loss per victim: $200,000
- Total losses in 2025: >$500 million
- Success rate: ~30% (attackers generate address, wait, hope victim copies it)
Recent High-Profile Cases:
- December 20, 2025: $50M USDT (this case)
- November 2025: $1.4M USDT lost to similar attack
- September 2025: $32M DAI stolen via address poisoning
- July 2025: Multiple victims lose combined $8M in coordinated campaign
This is not a “skill issue.” This is a systemic failure of wallet UX design across the entire ecosystem.
The Bottom Line (Or: Why We Can’t Have Nice Things)
A $50 million loss should not be possible because someone copied the wrong address from their transaction history. The fact that this attack is:
- Trivial to execute (3 seconds on a GPU)
- Impossible for humans to reliably defend against (perfect visual verification required)
- Completely preventable with existing technology (checksums have existed since 2016)
…is an absolute indictment of cryptocurrency wallet development.
Wallet developers have had NINE YEARS to implement EIP-55 checksum validation properly. They haven’t. They’ve had years to implement address book systems, visual verification tools, and sane transaction confirmation UX. They haven’t.
Instead, they ship wallets that:
- Display truncated addresses by default
- Don’t validate checksums
- Don’t warn about dust transactions from unknown addresses
- Don’t require additional confirmation for massive transfers
- Basically rely on users having superhuman attention to detail
And then when someone loses $50 million because they copy-pasted the wrong address, the response is: “Should have been more careful! Not your keys, not your crypto! DYOR!”
No. This is victim-blaming. This is developer negligence.
If you’re a wallet developer:
- Implement EIP-55 checksum validation with warnings
- Build a proper address book system
- Show full addresses (not truncated) for large transfers
- Add visual verification tools (identicons, blockies)
- Flag dust transactions from unknown addresses
- Require hardware wallet confirmation above a threshold
- Stop shipping UX that requires perfect human attention to avoid catastrophic loss
If you’re a user:
- NEVER copy addresses from transaction history
- Always use address book / saved contacts
- Verify checksums manually if your wallet won’t do it
- Use hardware wallets for any significant amount
- Always send a test transaction first (and wait to verify it arrived correctly before sending the real amount)
- Consider using ENS names instead of raw addresses
- Seriously reconsider using wallets with garbage UX
The technology to prevent this attack has existed for nine years. The fact that we’re still seeing $50 million losses in 2025 is an absolute failure of the crypto wallet development ecosystem.
Do better.
Timeline
- December 19, 2025: Victim sends $50 test transaction to legitimate address
- December 19, 2025: Attacker detects transaction, generates vanity address matching 3+4 chars
- December 19, 2025: Attacker poisons victim’s transaction history with dust transaction
- December 20, 2025: Victim copies poisoned address, sends $50M USDT
- December 20, 2025 (+30 min): Attacker converts to 16,690 ETH, begins laundering
- December 20, 2025 (+2 hours): Victim realizes mistake, attempts on-chain contact
- December 20, 2025 (+6 hours): Funds confirmed laundered through Tornado Cash
References
News Coverage:
- BeInCrypto: Whale Loses $50M USDT in Address Poisoning Scam
- Cointelegraph: Major USDT Loss Highlights Address Poisoning Threat
- CryptoSlate: $50M Address Poisoning Attack Analysis
On-Chain Analysis:
- Transaction Hash: View on Etherscan
- Victim Address:
0x12c6a709925783f49fc0c2bcE5D336f5a2dA25b8 - Attacker Address:
0x12c...[generated vanity]
Technical Resources:
- EIP-55: Mixed-case checksum address encoding
- Profanity2 GitHub - GPU vanity address generator (used in this demo)
- Profanity2 Security: Split-key cryptography
Tools:
- Google Colab - Free T4 GPU (used to generate the demo address in 4 seconds)
- Ethers.js - JavaScript library for key derivation
- MyEtherWallet Checksum Validator
- Etherscan Address Checksum Tool
Implement checksum validation. Use address books. Stop shipping wallets with UX that costs users $50 million.
And maybe, just maybe, consider that when your security model requires perfect human attention 100% of the time, you don’t have security - you have a time bomb.